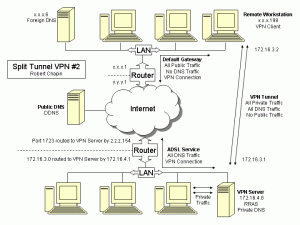
Two years ago, I devised a Windows XP split tunneling solution that involved static routing. That solution had the advantage of being cheap, but also had the disadvantage of scaling poorly with any number of client computers.
Now I have a second solution that eliminates the static routing problems.
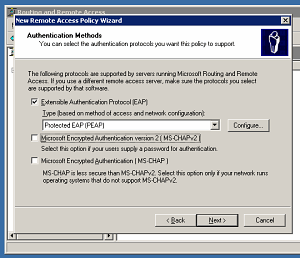
While researching new VPN security issues recently, I came across an obscure piece of information about the Windows VPN client. It is nestled cryptically in this one sentence from a Microsoft whitepaper:
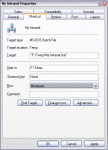
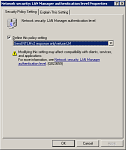
When the Use default gateway on remote network check box is cleared, a default route is not created, however, a route corresponding to the Internet address class of the assigned IP address is created.
Absent any other explanation, that sentence requires some mental gymnastics to understand. Allow me to help with this.